Nmap – Scan Timing & Performance
Nmap allows you to speed up and slow down scans based on the type of environment you are working in or targeting. This is very important as you may be dealing with network/business-critical infrastructure that might not be able to handle heavy/noisy scans, on the other hand, you may want to speed up larger types of scans. Slowing down scans can also help you evade IDS’s.
What we will be looking at:
- Timing Templates
- Parallelism
- Host group sizes
- Host timeout
- Scan delays
- Packet rate
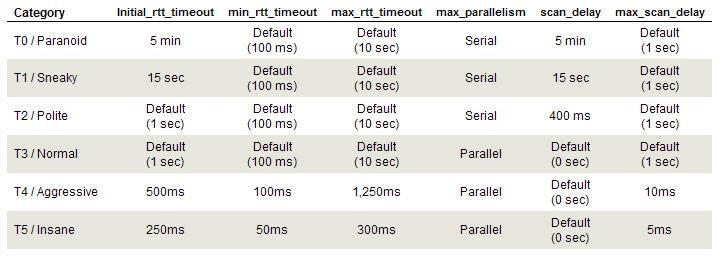
1) Timing Templates
- Timing templates are used to run scans faster or slower based on your target or working environment.
- The templates range from T0-T5, where T0 is the slowest and T5 is the fastest.
- Slower scans are very useful in evading IDS whereas faster scans are useful in larger scans.
- Faster scans can also be reliable in terms of the results.
- T3 is the default timing template used by Nmap.
Examples:
[simterm]nmap -T4 -sV nmap.scanme.org[/simterm]
[simterm]nmap -T1 -sV nmap.scanme.org[/simterm]
2) Parallelism
Parallelism is used to specify the number of parallel scanning processes is being run during a scan.
–min-parallelism is used to specify the minimum whereas –max-parallelism is used to specify the maximum.
Examples:
[simterm]nmap -sV –min-parallelism 10 nmap.scanme.org[/simterm]
[simterm]nmap -sV –min-parallelism 1 nmap.scanme.org[/simterm]
By default, Nmap will automatically determine the number of parallel operations to run based on the type of scan and network conditions.
3) Host Group Sizes
You can customize the minimum and maximum host group size when performing large scans that involve entire subnets. The host group size allows you to specify how many hosts to scan simultaneously.
–min-hostgroup –minimum
–max-hostgroup –maximum (Great when working with restraints)
Examples:
[simterm]nmap -sS -p21-443 –min-hostgroup 20 192.168.1.1/24[/simterm]
[simterm]nmap -sS -p21-443 –max-hostgroup 10 192.168.1.1/24[/simterm]
4) Host Timeout
Host timeout is used to specify the amount of time to elapse when scanning a target before skipping the host.
Example: If the target takes more than 30 seconds to respond, skip it.
- Some hosts may take a while to respond or may appear to be stuck based on various factors like connection and custom configs and firewalls. This can be used to speed up or slow down scans based on your target or network.
- This is very useful when performing large scans on subnets or on class b networks.
Example:
[simterm]nmap -Pn -p- 192.168.1-255.1-255 –host-timeout 30s[/simterm]
5) Scan Delays
- This allows you to pause Nmap for a specific amount of time between each probe/request.
- This is great for targets or systems that have some form of rate-limiting in place.
Example:
[simterm]nmap -sT –scan-delay 10s nmap.scanme.org[/simterm]
6) Packet Rate
This option allows you to specify the minimum and maximum amount of packets you want to send per second.
[simterm]nmap -sT –min-rate 20 nmap.scanme.org[/simterm]
Note: The higher the rate, the more unreliable the scan results.
[simterm]nmap -sT –max-rate 50 scanme.nmap.org[/simterm]