What is Docker?
Docker is a set of platform as a service products that use OS-level virtualization to deliver software in packages called containers. Containers are isolated from one another and bundle their own software, libraries, and configuration files; they can communicate with each other through well-defined channels.
- Docker allows you to build and deploy applications and services in the form of containers.
- It is a platform as a service offering that utilizes the host OS Kernel as opposed to a traditional VM, where OS’s have to be installed for every virtual machine.
- The containers contain the dependencies and libraries that that application or service needs to run, therefore eliminating the need for installing dependencies manually.
- Docker containers are much more efficient than VM’s as they utilize the host OS.
Docker vs VM’s
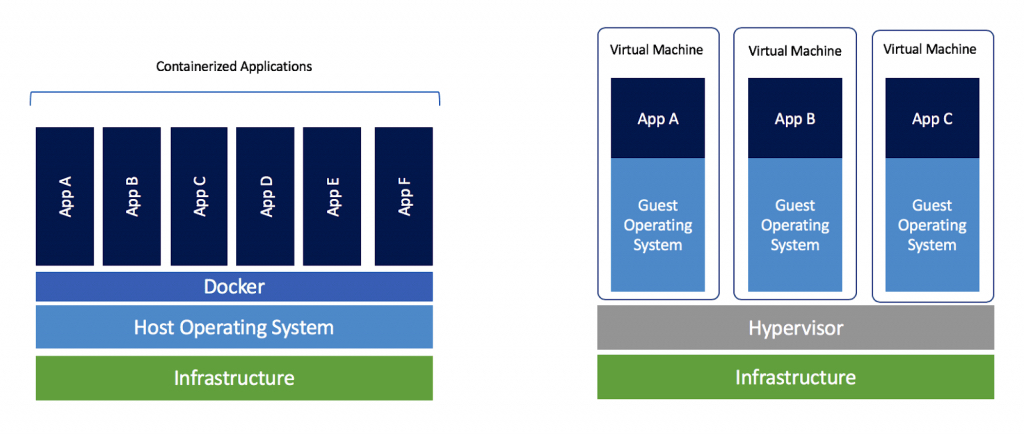
As you can see in the image, docker is much more efficient both in terms of setup time and resource consumption, as there are fewer layers that need to be virtualized. Additionally, docker can be installed and setup on all operating systems from Windows to Linux. The latter being the proffered deployment option for developers and DevOps teams.
Installing Docker on Linux
Docker can easily be installed on a multitude of Linux distributions, both through scripts or package managers. You can find the specific installation instructions on the Docker documentation page found at https://docs.docker.com.
You can install docker directly with the aptitude package manager on Ubuntu by running the following commands in the terminal:
Alternatively, you can follow the instructions provided by docker: https://docs.docker.com/install/linux/docker-ce/ubuntu/
After you have installed docker you should enable the service to be run on system startup, this can be done by utilizing systemd in the terminal:
After the service has been enabled, you can now start the docker service in the terminal to begin working with docker:
You can now test docker by running a simple command that will display active containers:
Since you do not have any active containers, we will not get any output.
Now that we have docker setup and running, we can begin working with docker images and containers.
Images & Containers
Images in docker are packaged services or environments and Docker containers are the running/active instances of these images. A simple analogy that explains this is that of a typical VM infrastructure, where the ISO is the image and the VM is the container.
We can access the multitude of docker images publicly available at https://hub.docker.com. Here you will find all the most popular services and technologies packaged up into convenient images for rapid and scalable deployment. For example, you can search to find a MySQL image that will automatically deploy a MySQL database in seconds.
Docker For Penetration Testing
Now that we have an understanding of how docker images and containers work, we can now get started by pulling an image and running it as a container with docker. In this case, we can try out the pre-built penetration testing OS images from Kali or Parrot. We also have vulnerable web apps that have been dockerized for easy and rapid deployment, for example, the OWASP Juice Shop project. Plenty of other dockerized images that can be used for pentesting and learning can be found on the docker hub.
To pull an image from the docker hub we can use the pre-set docker pull command on the docker repo page, this will download the image on your host for deployment, for example, we can pull the official Kali Linux Docker image by using the following command:
After the image has been pulled, we can confirm that it has been saved by accessing our local docker images, this can be done by running the following command:
This will display all our downloaded/saved images that we can deploy instantly. It also gives us vital information about the image like the repository name, the image ID, and the size. To create a container from an image we need to run the following commands:
This will run a kali Linux container with an interactive terminal session with bash. The syntax above and other options are specified below.
-
-it -Interactive Terminal
-
-d -Detached mode (This will run the container in the background)
-
--rm -Cleanup (This will delete the container after it has been put in an exited state.
After running the run command, we will be logged in to the Kali docker container with bash. We can now utilize the Kali repositories to install the various pen-testing tools that we require, this is because the Kali image does not contain any pre-installed tools. This is one of the disadvantages of running pen-testing images from Kali, they assume that docker can only be used to run a single tool or toolkit, whereas the technology can be leveraged to achieve a much more complete experience.
It is for this reason that I decided to undertake the process of building my own docker image that would contain all the necessary and important tools that are required for penetration testing or bug bounty hunting.
The Bug Bounty Toolkit
This is a multi-platform bug bounty toolkit that can be installed on Debian/Ubuntu or set up with Docker and offers all the popular tools that are used for pentesting and bug bounty hunting. The toolkit has been dockerized to utilize the reliability of docker when deploying environments. It can be pulled directly from our repository here: https://hub.docker.com/r/hackersploit/bugbountytoolkit.
You can also check out the installer script that has been designed to automatically install the tools on an Ubuntu/Debian-based distribution, this can be found on the official Github repository: https://github.com/AlexisAhmed/BugBountyToolkit where you can access and modify the Dockerfile to create a customized docker image.
Pulling and running the docker image is similar to running the Kali image, we can pull the image directly by using the following command in the terminal:
After the image has been pulled, we can create and run a container by running the following command in the terminal:
This will start the container and provide access through the specified shell. You can now run all your favorite tools on multiple containers with deployment times of less than 5 seconds.
Running Multiple Sessions
You can run multiple sessions/tools on the same container by utilizing the exec command. You can use the exec command to deploy more than one session for each container. This can be done by running the following command for every new session:
Running multiple sessions with Tmux
tmux is a terminal multiplexer for Unix-like operating systems. It allows multiple terminal sessions to be accessed simultaneously in a single window. It is useful for running more than one command-line program at the same time.
Feel free to contribute to the project or get in touch if you have any issues. We appreciate your feedback and would like to hear more about how you can leverage Docker for and in penetration testing.
Running Docker On Windows
If you would like to run Docker on Windows, you can watch our video on the subject where we cover the installation process and the various requirements needed for running Docker on Windows systems.


