In this presentation, I explain the importance of Docker and how it can be utilized for pentesting & bug bounty hunting. I also showcase how to set up Kali Linux, OWASP Juice Shop & Bug Bounty Toolkit on Docker. Docker is a set of platform as a service products that use OS-level virtualization to deliver software in packages called containers. Containers are isolated from one another and bundle their own software, libraries, and configuration files; they can communicate with each other through well-defined channels.
What is Docker?
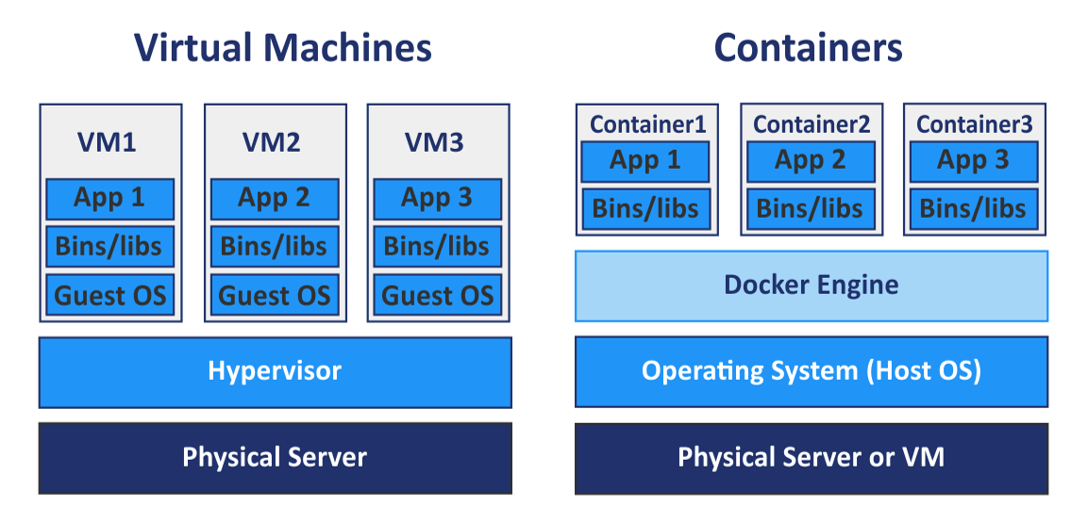
Docker is a platform as a service (PaaS) offering that utilizes the host OS Kernel as opposed to hypervisors like VMware.
Docker allows you to build and deploy applications and services in the form of containers.
The containers contain the dependencies and libraries that that application or service needs to run, therefore eliminating the need for installing dependencies and managing the OS.
Docker containers are much more efficient than VM’s as they utilize the host kernel.
Docker VS Virtual Machines
Advantages of using Docker for pentesting & bug bounty hunting
- Provides a multi-platform solution/base for running containers.
- Containerized offensive distributions like Kali and Parrot with full repo support.
- Containerized vulnerable web apps like OWASP Juice Shop, DVWA that can be used for training and learning.
- Pentesting & bug bounty toolkits.
- Resource efficient.
- Tools and images can easily be updated.
Links used in presentation
- BugBountyToolkit: https://github.com/AlexisAhmed/BugBountyToolkit
- Kali Linux: https://hub.docker.com/r/kalilinux/kali-linux-docker
- OWASP Juice Shop: https://hub.docker.com/r/bkimminich/juice-shop


