What is Google Hacking/Dorking?
Google hacking is a passive information gathering/footprinting technique that is used to discover vulnerabilities, data exposure, and security misconfigurations in websites. It involves using specialized search query operators to finetune results based on what you are looking for.
Common Google search query operators
site: Narrows results to a site or a specific TLD. Example: site:hsploit.com intitle: Restricts results to titles of webpages. Example: intitle:”HackerSploit” inurl: Restricts results to the URL of a website. Example: inurl:about filetype: Searches for specific filetypes based on the extensions. Example: filetype:pdf link: Searches for pages linking to a specified URL. Example: link:www.hsploit.com cache: Searches for a cached copy of a webpage when it was indexed by Google. Example: cache:hsploit.com
To learn more about the other search operators, please refer to the sources at the bottom of the page or, alternatively, the image below explains the use-case and the scope of functionality of Google search operators.
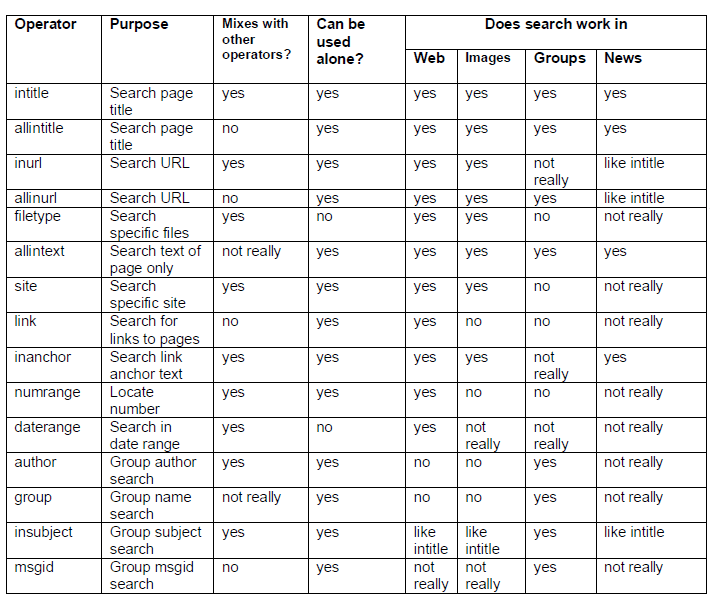
Google hacking for penetration testing
The following are a list of search queries that can be used to discover vulnerabilities, misconfigurations, admin panels, and credentials of companies and their respective websites/domains.
Credentials and serials
site:pastebin.com gmail
Personal details
site:pastebin.com intitle:john ssn
File Types
intitle:kali filetype:iso
Directory Listing
intitle:"Index of"
etc directory listing
intitle:index.of.etc
intitle:index.of.etc.passwd
SQL Database credentials or config files
intitle:"Index of" config.php
intitle:"Index of" wp-config.php
Microsoft database files
allinurl:admin filetype:mdb
Terminal Servers on the web
inurl:tsweb
Auth User files
allinurl:auth_user_file.txt
Credentials
login: * password= * filetype:xls
Using the Google Hacking Database (GHDB)
The GHDB is a database/collection of Google search queries specifically crafted to find vulnerabilities, misconfigurations, and data exposure. You can use the GHDB to find strings and search queries to fine-tune results based on the information/vulnerabilities you are looking for.


