Installing Lynis
Lynis is an extensible security audit tool for computer systems running Linux, FreeBSD, macOS, OpenBSD, Solaris, and other Unix derivatives. It assists system administrators and security professionals with scanning a system and its security defenses, with the final goal being system hardening.
Lynis is available as a package for most Linux distributions, we can install it by running the following command:
[simterm] $ sudo apt install lynis [/simterm]
To display all the options and commands available, we can run the following command:
[simterm] $ lynis show options [/simterm]
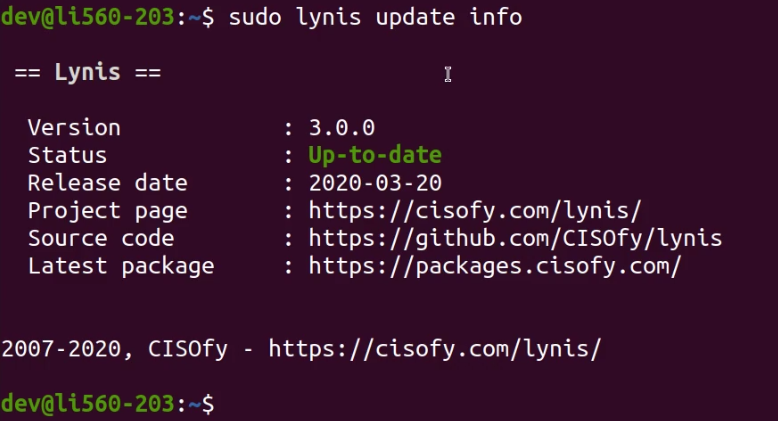
Before we get started with scanning, we need to ensure that Lynis is up to date. To check if we are running the latest version we can run the following command:
[simterm] $ sudo lynis update info [/simterm]
System Auditing With Lynis
To perform a system audit with Lynis we run the following command:
[simterm] $ sudo lynis audit system [/simterm]
Lynis will output a lot of information that will also be stored under the /var/log/lynis.log file for easier access. The summary of the system audit will reveal important information about your system’s security posture and various security misconfigurations and vulnerabilities.
Lynis will also generate output on how these vulnerabilities and misconfigurations can be fixed or tweaked.
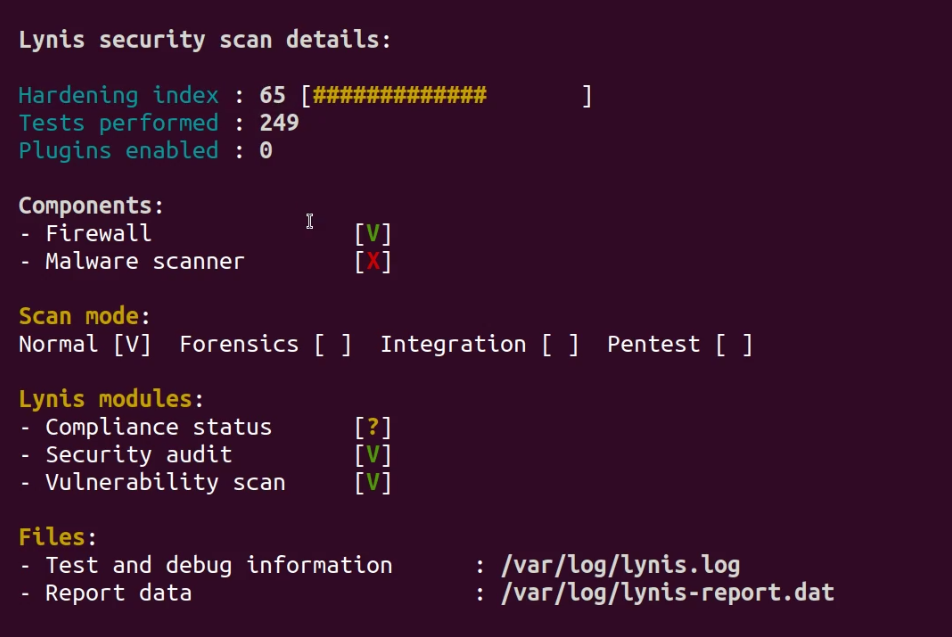
The output also contains a hardening index score that is rated out of 100, this is used to give you a trackable tangible score of your system’s current security posture.
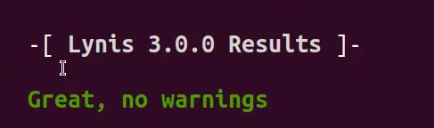
Lynis will also display any potential warnings that will indicate a severe security vulnerability or misconfiguration that needs to be fixed or patched, in this case, we have no warnings.
To increase our hardening index score, Lynis provides us with helpful suggestions that detail the various security configurations we need to make.
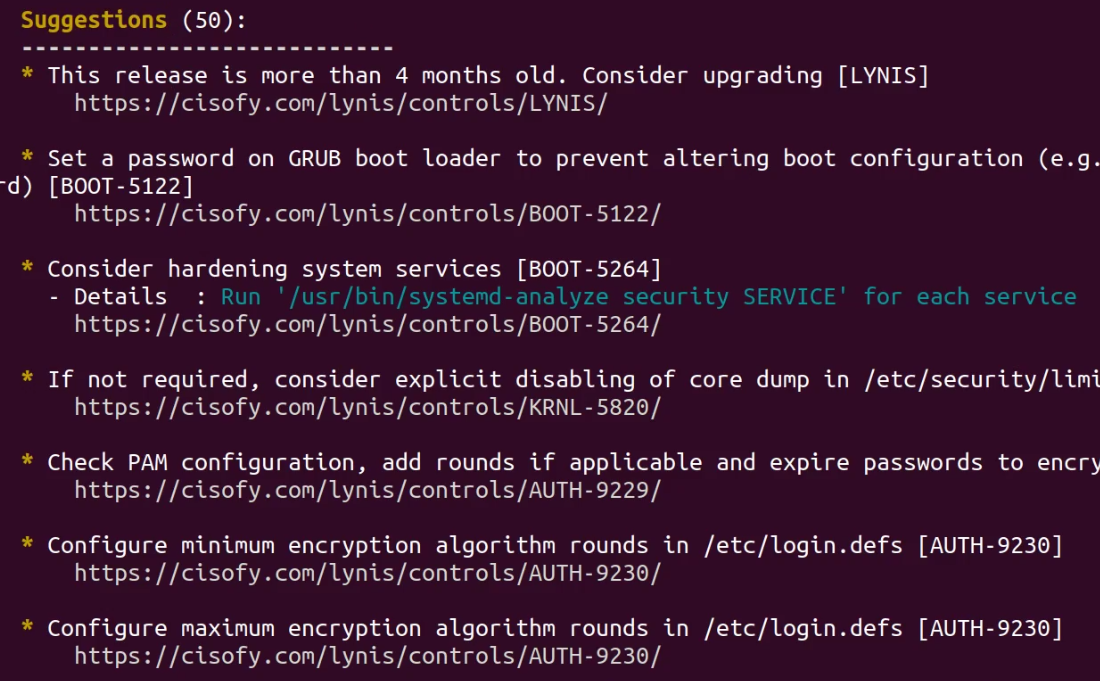
After following the suggestions and making the necessary changes, we can run the system audit with Lynis again.
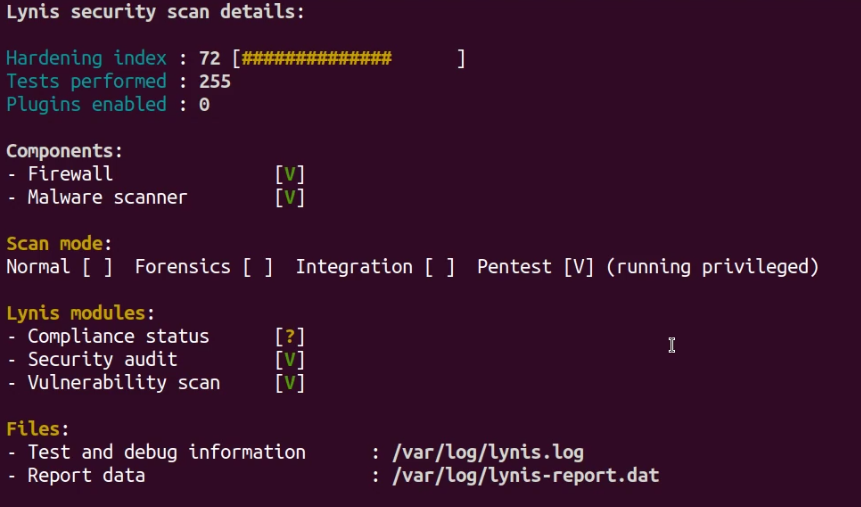
As shown above, there is a significant improvement in the hardening index score that confirms the changes and configurations we made are applied and effective.
Pentest With Lynis
Lynis also has the ability to simulate a privileged/internal pentest on the system, this can be invoked by using the following command:
[simterm] $ sudo lynis –pentest [/simterm]
This will perform a pentest on the system and will output a hardening index score that reflects the overall security posture of the system.


